《1. Introduction》
1. Introduction
To support the surging growth of wireless data traffic while meeting the requirements for high data rates in next-generation cellular networks, heterogeneous cellular networks (HCNs) are emerging as a promising solution to enable a significant leap in network performance [1–4]. By densely deploying hierarchical infrastructure in different tiers (i.e., macro base stations (MBSs), micro base stations (mBSs), pico base stations (BSs), femto base stations, and relays) and permitting them to transmit information simultaneously over the same spectrum band, the HCNs are capable of achieving seamless coverage and accommodating more users. Motivated by the great potential, the investigation of the HCNs has received substantial interest [5–7].
Despite the benefits brought by HCNs, there are some challenging issues that should be further investigated. On the one hand, Despite the benefits brought by HCNs, there are some challenging issues that should be further investigated. On the one hand, there are massive communication terminals coexisting in different tiers of HCNs and sharing limited spectrum resources. Therefore, unlike conventional single-tier cellular networks where data transmission is hampered mainly by malicious jamming, substantial intra- and inter-tier interference exists in HCNs, which reduces the success probability and reliability of data transmission. On the other hand, due to the open system architecture and the broadcast nature of radio propagation, confidential messages intended for authorized users are vulnerable to eavesdropping attacks.
Recent advances in interference and eavesdropping technologies in communication networks [8–12] further exacerbate the security risks in HCNs. Based on the report of risk-based security (RBS) in the third quarter of 2019 [13], there were 5183 data leakage events around the world in the first nine months of 2019. In view of the fact that wireless networks have been introduced into many fields (such as intelligent manufacturing [14], smart healthcare [15], and the Internet of Things [16,17]), the negative impact of data leakage on wireless network security has captured both industry and academia attention. When private information cannot be transmitted reliably and securely, serious consequences can occur, including property damage (e.g., disruption of industrial production chains, traffic congestion) and even personnel casualties (e.g., medical malpractice, traffic collisions).
Therefore, it is crucial to guarantee reliable and successful data transmission in HCNs while addressing interference and eavesdropping threats. However, the design of the transmission scheme is a daunting task in HCNs for the following reasons. First, the transmission scheme design should not only address the interference and eavesdropping threats but also improve the network capacity in HCNs. Considering the limited spectrum resources, dynamic spectrum control (DSC) is required to enable more authorized users to access HCNs without causing harmful interference. Second, to improve the security performance, authorized data transmission should occupy different frequency slots during the transmission period to make it intractable for eavesdroppers to intercept the transmitted information. Furthermore, reliable transmission and secure transmission probabilities should be analyzed and provided to evaluate the performance of the transmission scheme in HCNs.
《1.1. Related work》
1.1. Related work
In the literature, there are many studies on interference management and security enhancement [18–22]. Lv et al. [18] pioneered the study of physical layer security in downlink two-tier heterogeneous networks (HetNets) and optimized the secrecy rate performance by designing a beamforming scheme. Subsequently, Wang et al. [19] considered the randomness of the spatial location of network nodes and proposed a secrecy mobile association policy based on the access threshold, which provided a basic analytical framework to evaluate the secrecy performance of HCNs. Xu et al. [20] introduced cooperative multipoint transmission (CoMP) into the construction of HetNets to enhance the secured coverage probability. Inspired by the aforementioned methods, an interference-canceled opportunistic antenna selection (IC-OAS) scheme was proposed in Ref. [21] to improve the potential of the security–reliability tradeoff of macrocells and microcells. In Ref. [22], the secrecy energy efficiency (EE) was optimized by introducing artificial noise into orthogonal frequency division multiplexing (OFDM)-based cognitive radio networks with different base stations.
However, the aforementioned methods mainly focus on the security and interference issues of HCNs, while ignoring the everincreasing wireless network traffic that should be handled by limited spectrum resources. In fact, the scarce spectrum resources available to support wireless communications services are underutilized. Therefore, it is essential to design an effective transmission scheme to improve the spectrum utilization efficiency and increase the network capacity of HCNs.
To mitigate spectrum scarcity in HCNs, some initiatives have been investigated in the past decade [23–26]. To improve the spectrum efficiency (SE) and EE under quality-of-service (QoS) constraints in multi-tier HetNets simultaneously, Rao and Fapojuwo [23] and Al Masri and Sesay [24] verified that traffic offloading is an effective approach. However, the performance gain brought by offloading is strongly affected by intra- and inter-tier interference. Yang et al. [25] pointed out that inter-tier interference is the main bottleneck for increasing network capacity in HetNets and proposed an F-ALOHA based cognitive spectrum access scheme for macro–femto HetNets. This scheme incorporated the idea of cross-tier spectrum access to offload traffic, thereby achieving interference management and optimization of SE. In addition, another spectrum flowing scheme that can trade or lease the licensed spectrum among tiers or network nodes to minimize spectrum holes was proposed in Ref. [26].
In summary, network capacity improvement and security enhancement have attracted substantial research interest. Although HCNs can effectively increase network capacity, the densified network architecture introduces cross-tier interference, which might further aggravate the threats to network security. The existing works focus either on network capacity improvement or transmission security enhancement in HCNs, failing to address both issues in HCNs. On the one hand, the aforementioned endeavors to cope with transmission security threats consume additional power and signal overhead, which might introduce extra interferences and hamper the network capacity performance. On the other hand, the existing approaches for increasing network capacity can effectively address the interferences in HCNs, but cannot overcome the threats of eavesdropping. To the best of our knowledge, there is no existing analysis of HCNs by jointly considering security and network performance. However, only by jointly considering the two performances together can HCNs meet the requirements of authorized users in real-world applications. This has motivated our work. In this work, we focus on the transmission scheme design in HCNs to effectively improve network capacity while guaranteeing security performance.
《1.2. Main contributions》
1.2. Main contributions
In this article, we propose a transmission scheme based on DSC for HCNs. By sensing the occupation status of the spectrum resources, the proposed scheme can generate a set of decisions by leveraging the idea of block cryptography and performing iterative and orthogonal operations. Based on these decisions, the data transmission can effectively occupy the idle frequency slots in each time slot. In addition, based on the analysis of the collision probability caused by multiple data packets occupying the same frequency slot in a time slot, the closed-form expressions of the reliable transmission probability (i.e., the data packets can be completely transmitted to authorized receivers) and secrecy probability (i.e., the data packets cannot be acquired by eavesdroppers) are derived from the idea of information-theoretic security [27]. Furthermore, under the constraints of reliable transmission probability and secrecy probability, the upper and lower bounds of network capacity can be determined. Therefore, by employing the DSC-assisted transmission scheme, the goal of strengthening the security and improving the network capacity of HCNs can be achieved. The main contributions of this article can be summarized as follows:
• We propose a DSC-assisted transmission scheme, which can guide the data packets to occupy the frequency slots in each time slot by generating orthogonal sequences. By scheduling communication links in an orderly manner, the proposed scheme can effectively reduce interference and make it more intractable for eavesdroppers to intercept transmitted privacy information.
• We theoretically analyze the collision probability of multiple data packets occupying the same frequency slot in a time slot, which provides the theoretical foundation for security and network capacity analysis in HCNs.
• We define the reliable transmission probability and secrecy probability of the proposed transmission scheme in HCNs and derive their closed-form expressions, which provides an analytical framework for evaluating the security performance of HCNs. Based on these two probabilities, the network capacity of HCNs under security constraints can be determined.
• We verify that the proposed DSC-assisted scheme can outperform the conventional secure transmission scheme in terms of security performance, which can be further improved by adjusting the network parameters. In addition, the maximum number of users allowed to associate with HCNs can be adjusted according to the actual security requirements.
The remainder of this article is organized as follows. Section 2 depicts the system model. Then, the proposed DSC-assisted transmission scheme is presented in Section 3. Based on the proposed scheme, the security analysis in HCNs (including reliable transmission probability and secrecy probability) is conducted in Section 4. In Section 5, we evaluate the network capacity. After that, the simulation results are shown in Section 6, followed by the conclusion and future work in Section 7.
《2. System model》
2. System model
Based on real-world application scenarios and the existing HCNs models [28–32], a typical multi-tier HCNs scenario is considered in this work as shown in Fig. 1. The HCNs consist of one MBS, multiple mBSs, several authorized users, and randomly located passive eavesdroppers. Let {BSφ | φ = (1, 2, ..., m, M)} denote the base stations in the scenario with different clocks, where m is a positive integer representing the number of mBSs and M is a symbol representing the MBS. In addition, φ  {1, 2, ..., m} represents the mBS and φ = M refers to the MBS. These base stations are equipped with multiple antennas to support the communication of multiple authorized users simultaneously. In the considered HCNs scenario, the BSM covers the entire network to form a macrocell and can serve authorized users with a high transmission power PBS (from 5 to 40 W), where PBS is the power of the BSM. To handle the ever-growing traffic requirement and achieve seamless coverage, several BSms can be deployed within the macrocell. Different from the BSM, BSms have smaller coverage radii and form multiple microcells that do not overlap with each other thus they can only serve the authorized users within their coverage areas with a lower transmission power Pbs (from 250 mW to 2 W), where Pbs is the power of the BSm. Since it is almost impossible to accurately determine the instantaneous channel state information (CSI) of passive eavesdroppers in practice, only statistical CSI of the channels is available in our work, as assumed in many previous works [33– 35]. Without loss of generality, we assume that each communication link in our constructed HCNs experiences independent flat Rayleigh fading such that the channel power gains are exponentially distributed. Specifically, the mean value of the channel power gain is |hu| 2 between the BSM and authorized users, |he| 2 between the BSM and eavesdroppers, |hmu| 2 between the BSm and authorized users, and |hme| 2 between the BSm and eavesdroppers.
{1, 2, ..., m} represents the mBS and φ = M refers to the MBS. These base stations are equipped with multiple antennas to support the communication of multiple authorized users simultaneously. In the considered HCNs scenario, the BSM covers the entire network to form a macrocell and can serve authorized users with a high transmission power PBS (from 5 to 40 W), where PBS is the power of the BSM. To handle the ever-growing traffic requirement and achieve seamless coverage, several BSms can be deployed within the macrocell. Different from the BSM, BSms have smaller coverage radii and form multiple microcells that do not overlap with each other thus they can only serve the authorized users within their coverage areas with a lower transmission power Pbs (from 250 mW to 2 W), where Pbs is the power of the BSm. Since it is almost impossible to accurately determine the instantaneous channel state information (CSI) of passive eavesdroppers in practice, only statistical CSI of the channels is available in our work, as assumed in many previous works [33– 35]. Without loss of generality, we assume that each communication link in our constructed HCNs experiences independent flat Rayleigh fading such that the channel power gains are exponentially distributed. Specifically, the mean value of the channel power gain is |hu| 2 between the BSM and authorized users, |he| 2 between the BSM and eavesdroppers, |hmu| 2 between the BSm and authorized users, and |hme| 2 between the BSm and eavesdroppers.
《Fig. 1》
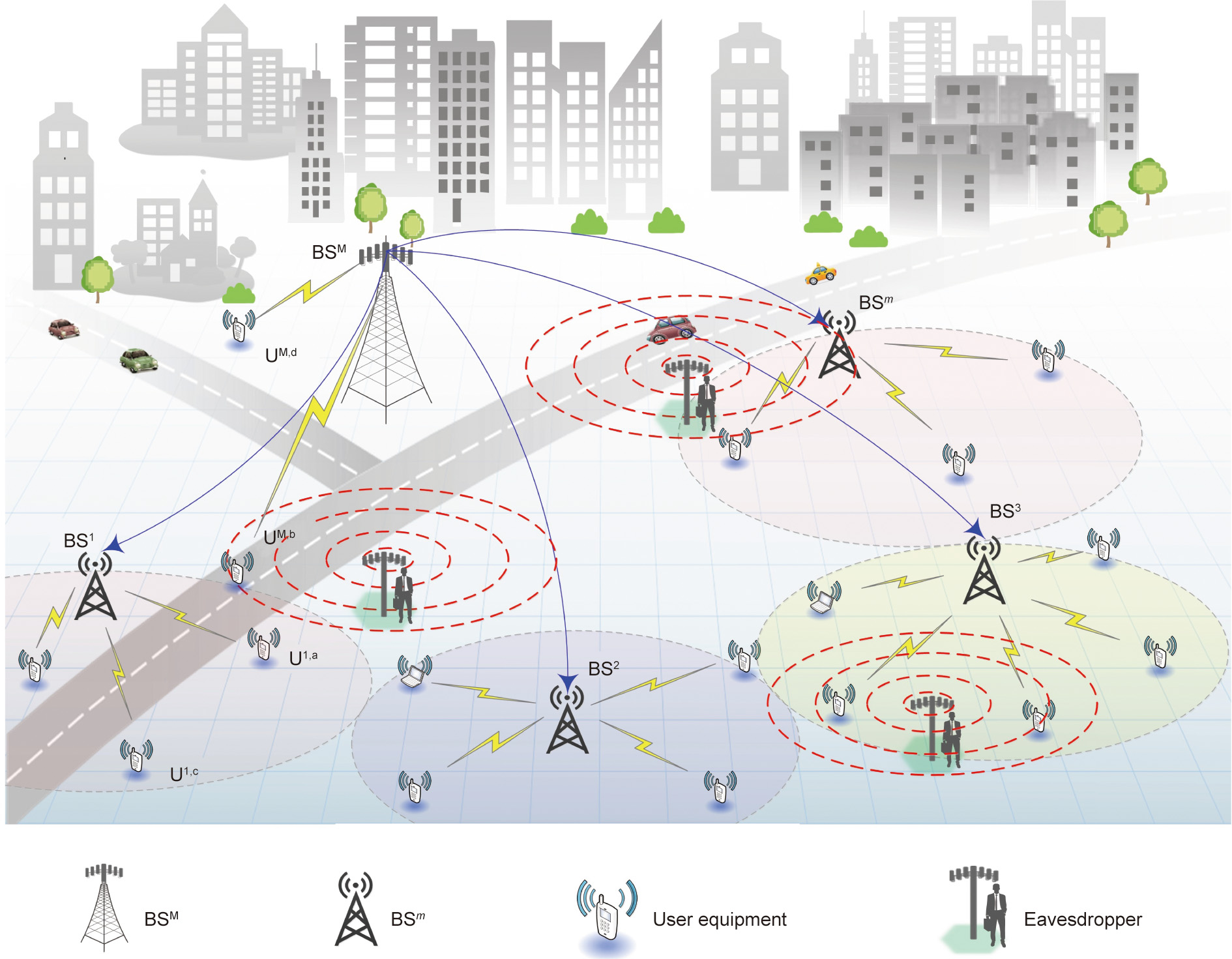
Fig. 1. Illustration of the HCNs. BSM: MBS; BSm: mBS; UM,d: the authorized user d associated with the BSM; UM,b: the authorized user b associated with the BSM; U1,a: the authorized user a associated with the BS1 ; U1,c: the authorized user c associated with the BS1 .
Specifically, we focus on the downlink transmission for the authorized users, where data packets are transmitted by the base stations independently over the shared transmission channel. Without loss of generality, the authorized users Uk (k = 1, 2, ..., K) can choose to associate with the BSM or BSms based on the signal-to-interference-plus-noise ratio (SINR) of downlinks in HCNs [36], where K is a positive integer representing the total number of the authorized users and k represents one of them.
As shown in Fig. 1, there are many potential threats affecting the transmission performance between base stations and users (e.g., unfriendly jammers, uncooperative interference, and malicious eavesdropping). Specifically, unfriendly jammers existing in the service area might randomly send interference signals to occupy the transmission band, which reduces the quality of the communication link and even tamper with the transmitted information or interrupt communication. In addition, since the BSM and BSms share the same frequency band, the signals transmitted by the BSM are regarded as uncooperative interference for the authorized users in the BSms, and vice versa. Furthermore, considering the small geographical area covered by each BSm, authorized users occupying the same frequency band served by the same BSm can interfere with each other. However, the most malicious one is the eavesdroppers, as shown in Fig. 1, who can be randomly distributed and desire to intercept the privacy information transmitted by authorized users with the assistance of an energy detector (e.g., a radiometer).
《3. DSC-assisted transmission scheme》
3. DSC-assisted transmission scheme
To cope with the aforementioned threats effectively, an effective transmission scheme for assisting asynchronous networking is proposed in this section to strengthen the security of HCNs and facilitate the realization of superior network performance.
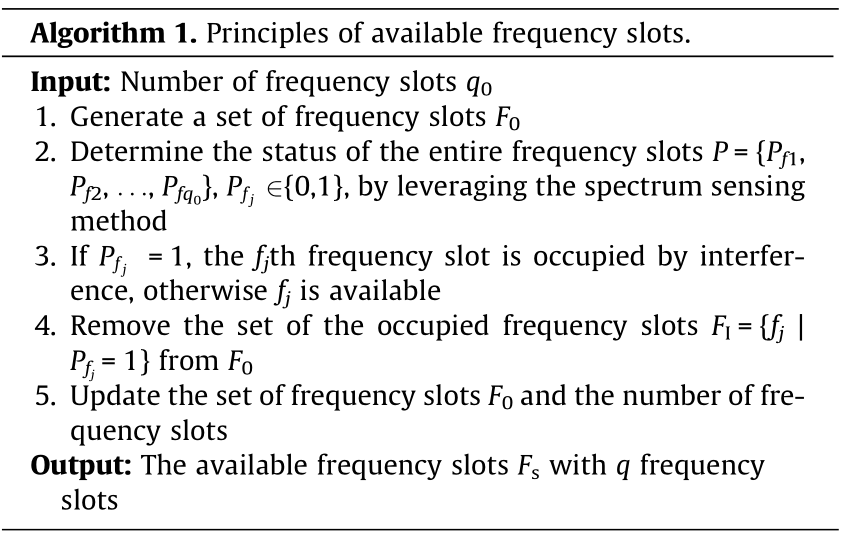
Without loss of generality, all authorized users transmit their data packets on a discrete-time channel with p time slots (t1, t2, ..., tp), where p is a positive integer representing the total number of divided time slots, and tp is the pth time slot. We assume that the transmitted data packets of authorized users in our considered HCNs need to occupy L consecutive time slots to complete their transmissions in each transmission period, where L represents the length of the transmitted data packets. Authorized users who desire to transmit information with a large data volume may require multiple transmission periods to complete the transmission of all information. In addition, to address the contradiction between the increasing number of authorized users and the limited spectrum resources, we divide the shared transmission bandwidth into q0 non-overlapping frequency slots in advance, which constitute the set of frequency slots F0 = {f1, f2, ..., fq0 }, where q0 is a positive integer representing the initial value of the divided frequency slots, and fq0 denotes the q0th frequency slot. Note that the frequency slots in F0 cannot only be used by authorized users, but also be occupied by interference signals. Furthermore, considering that passive eavesdroppers can intercept data transmission, in the designed transmission scheme, every frequency slot can only be occupied by each user no more than once during a transmission period to make it intractable for eavesdroppers to decode the transmitted information. Therefore, we propose a DSC-assisted transmission scheme as follows to enhance the security of the network we are considering.
To tackle the negative impact of malicious interference, each base station leverages the spectrum sensing method within F0 to determine the occupation status of each frequency slot in our proposed DSC-assisted transmission scheme. In recent decades, many refined spectrum sensing methods have been proposed [37–39], including spectrum sensing methods based on energy detection, eigenvalues, high-order cumulants (HOCs), and so forth. Here, we choose the HOCs-based spectrum sensing method to provide us with the occupation status of each frequency slot, since this method can extract a non-Gaussian signal from Gaussian noise even when the noise is colored and eliminate the adverse effects of noise power uncertainty in practical applications. According to the sensing results, the status of the frequency slots (P) can be expressed as P = {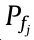 | j = 1, 2, ..., q0}, where j is the number of the frequency slots, the
| j = 1, 2, ..., q0}, where j is the number of the frequency slots, the 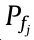 represents the status of the jth frequency slot and
represents the status of the jth frequency slot and 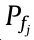
 {0,1}. If
{0,1}. If 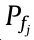 = 1, the jth frequency slot
= 1, the jth frequency slot  is already occupied, otherwise frequency slot
is already occupied, otherwise frequency slot  can be accessed. Finally, the base station can remove the interfered frequency slots from F0 and acquire the set of available frequency slots Fs with q frequency slots, where q indicates the number of idle frequency slots. Consequently, the BSφ should select and allocate frequency slots from Fs for the authorized users to ensure secure and reliable data transmission over a transmission period (t1–tp). The detailed procedure of determining Fs is described in Algorithm 1.
can be accessed. Finally, the base station can remove the interfered frequency slots from F0 and acquire the set of available frequency slots Fs with q frequency slots, where q indicates the number of idle frequency slots. Consequently, the BSφ should select and allocate frequency slots from Fs for the authorized users to ensure secure and reliable data transmission over a transmission period (t1–tp). The detailed procedure of determining Fs is described in Algorithm 1.
In the considered HCNs, each BSφ can provide guidance for its local users to select which frequency slots to occupy in each time slot, thus completing data packet transmission successfully in an orderly manner. LetUφ,k denote user Uk, which is served by BSφ. Thus, the frequency slots occupied by Uφ,k during a transmission period can be presented by a DSC sequence 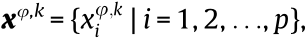 where
where 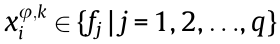 representstheuser Uφ,k should occupy the jth frequency slot over the ith time slot to complete the packet transmission. Fig. 2 gives an example of the transmission decisions of Ua associated with BS1
representstheuser Uφ,k should occupy the jth frequency slot over the ith time slot to complete the packet transmission. Fig. 2 gives an example of the transmission decisions of Ua associated with BS1  Ub associated with BSM
Ub associated with BSM  obtained by the proposed DSC-assisted scheme. As shown in Fig. 2, the DSC-assisted transmission scheme provides a sequence
obtained by the proposed DSC-assisted scheme. As shown in Fig. 2, the DSC-assisted transmission scheme provides a sequence 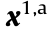 =
= 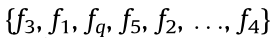 for U1,a associated with BS1 , and a sequence
for U1,a associated with BS1 , and a sequence  =
= 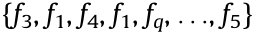 for UM,b controlled by BSM .
for UM,b controlled by BSM .
In the following, we propose a DSC-assisted transmission scheme that can be dynamically adjusted based on the spectrum sensing results with superior security performance. The DSC-assisted transmission scheme can generate a family of DSC sequences to represent the transmission decisions of the authorized users. With the proposed scheme, multiple authorized users can receive the data packets reliably during the same period and the possibility for passive eavesdroppers to decipher the transmission scheme is reduced, thereby achieving the goal of secure communication for authorized users. The procedures of generating the proposed DSC-assisted transmission scheme can be summarized in Algorithm 2.
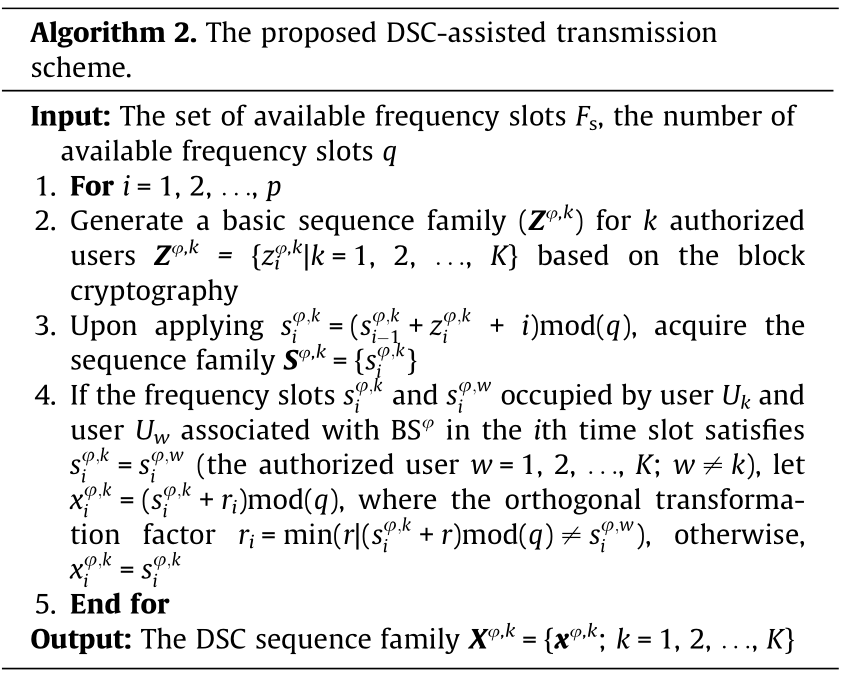
Specifically, the detailed steps are as follows:
• Generate a basic sequence: A random basic sequence Zφ,0 = 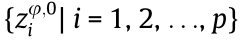 for an authorized user Uφ,0 should be generated by the time of day (TOD) series ti (i = 1, 2, ..., p) and the identification of the user’s key.
for an authorized user Uφ,0 should be generated by the time of day (TOD) series ti (i = 1, 2, ..., p) and the identification of the user’s key. 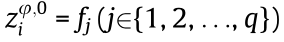 representsthat Uφ,0 occupies the fjth frequency slot to transmit its data packet at the ith time slot. To simultaneously provide k
representsthat Uφ,0 occupies the fjth frequency slot to transmit its data packet at the ith time slot. To simultaneously provide k (1, 2, ..., K) users with transmission decisions that are hard to crack by the passive eavesdroppers, this basic sequence should be extended into a group containing k sequences.
(1, 2, ..., K) users with transmission decisions that are hard to crack by the passive eavesdroppers, this basic sequence should be extended into a group containing k sequences.
• Expanding the basic sequence by iterative operations: In light of the block cipher algorithm [40], the initial iteration factor 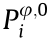 which generates
which generates  is iterated for k rounds as
is iterated for k rounds as 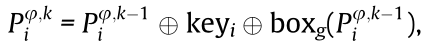 where
where  denotes the exclusive OR operation, key i is the identification symbol of the authorized users associated with BSφ in the ith time slot, and g (g = 1, 2, 3, ...) is the number of the iterative operation box. Therefore, a group of basic sequences
denotes the exclusive OR operation, key i is the identification symbol of the authorized users associated with BSφ in the ith time slot, and g (g = 1, 2, 3, ...) is the number of the iterative operation box. Therefore, a group of basic sequences 
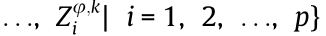 can be obtained as
can be obtained as 
 Then, comparing
Then, comparing 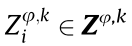 with the optimal decision threshold value can produce two different mappings. If
with the optimal decision threshold value can produce two different mappings. If  is less than the threshold value,
is less than the threshold value, 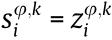 , otherwise
, otherwise  mod(q). Therefore,
mod(q). Therefore, 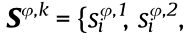
 can be acquired.
can be acquired.
• Orthogonalize the group of sequences: When 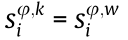 (w = 1, 2, ..., K; w ≠ k), we can acquire
(w = 1, 2, ..., K; w ≠ k), we can acquire 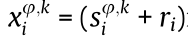 mod(q), where the orthogonal transformation factor ri = min(r|
mod(q), where the orthogonal transformation factor ri = min(r|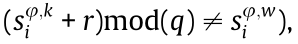 otherwise,
otherwise, 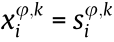 . Therefore, a DSC sequence family
. Therefore, a DSC sequence family 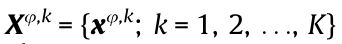 is obtained, where the sequence
is obtained, where the sequence 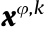 represents the frequency slots occupied by Uφ,k to transmit data packets during the transmission period.
represents the frequency slots occupied by Uφ,k to transmit data packets during the transmission period.
• Based on the generated DSC sequence family 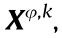 authorized users can occupy idle frequency slots in each time slot. It is clear that authorized users in the same microcell can access this micronetwork synchronously under the control of the mBS. Since the clocks are different in diverse microcells, the users associated with different mBSs and the MBS access the shared spectrum resources asynchronously. As shown in Fig. 2, two authorized users in different communication cells (U1,a and UM,b) transmit the data packet occupying L (L ≤ p ≤ q) consecutive time slots independently and randomly.
authorized users can occupy idle frequency slots in each time slot. It is clear that authorized users in the same microcell can access this micronetwork synchronously under the control of the mBS. Since the clocks are different in diverse microcells, the users associated with different mBSs and the MBS access the shared spectrum resources asynchronously. As shown in Fig. 2, two authorized users in different communication cells (U1,a and UM,b) transmit the data packet occupying L (L ≤ p ≤ q) consecutive time slots independently and randomly.
《Fig. 2》

Fig. 2. Schematic diagram of the transmission scheme. fq: the qth frequency slot.
《4. Security analysis of data transmission in HCNs》
4. Security analysis of data transmission in HCNs
In this section, we conduct a theoretical analysis of the collision probability between two authorized users employing the DSCassisted transmission scheme. Based on the analysis of the collision probability, we also derive the closed-form expressions of the probability that authorized users can reliably receive the transmitted data packets and the probability that the eavesdroppers cannot acquire the transmitted data packets.
《4.1. Collision probability》
4.1. Collision probability
Considering that the TODs of these communication cells are different, authorized users in the MBS and mBSs might occupy the same frequency slot simultaneously, which causes a collision and introduces transmission interference. We assume that the process of data packets arriving at the shared transmission channel follows a Poisson distribution with an arrival rate (G).
Consequently, the probability density function (PDF) of transmitting data packets n in L time slots can be presented by fPDF(n).

Note that the interference caused by the authorized data transmission in the HCNs is much greater than the interference power of the background noise. Therefore, the collision probability of data transmission should be analyzed since it greatly affects the data transmission performance. In our constructed HCNs, the collision probability for an authorized user refers to the probability that the authorized user occupies the same frequency slot as others in the same time slot when transmitting data packets in this network. Note that with the proposed DSC-assisted transmission scheme, authorized users served by the same base station do not collide with each other following the orthogonal sequences. Therefore, the data transmitted by the MBS can only conflict with the data transmitted by the mBS. Furthermore, considering that the coverage areas of the mBSs do not overlap with each other, an authorized user served by an mBS can only conflict with the data transmission from the MBS. In the following, we analyze the collision probability between users U1,a (associated with BS1 ) and UM,b (associated with the BSM) when transmitting their data packets.
The data packet transmission processes of U1,a and UM,b that are located in the BS1 cell are shown in Fig. 3. The symbols 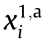 (i = 1, 2, ..., L) and
(i = 1, 2, ..., L) and 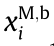 in Fig. 3 correspond to the frequency slots that are occupied by U1,a and UM,b at the ith time slot, respectively. Considering that the clocks of different cells are independent of each other, the data transmission start time of UM,b might not be aligned with that of U1,a. As shown in Fig. 3, UM,b does not start transmitting until U1,a is about to complete the transmission task of the second time slot. We assume that there are
in Fig. 3 correspond to the frequency slots that are occupied by U1,a and UM,b at the ith time slot, respectively. Considering that the clocks of different cells are independent of each other, the data transmission start time of UM,b might not be aligned with that of U1,a. As shown in Fig. 3, UM,b does not start transmitting until U1,a is about to complete the transmission task of the second time slot. We assume that there are  time slots overlapping between these two packets during the transmission period. In this case, during the data transmission period of UM,b, every time slot
time slots overlapping between these two packets during the transmission period. In this case, during the data transmission period of UM,b, every time slot 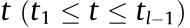 of UM,b overlaps with two consecutive time slots of U1,a, the lth time slot of UM,b only overlaps with the Lth time slot of U1,a, and the remaining time slots of UM,b do not overlap with U1,a. It is worth noting that there is a special case where only the first time slot of UM,b overlaps with the last time slot of U1,a.
of UM,b overlaps with two consecutive time slots of U1,a, the lth time slot of UM,b only overlaps with the Lth time slot of U1,a, and the remaining time slots of UM,b do not overlap with U1,a. It is worth noting that there is a special case where only the first time slot of UM,b overlaps with the last time slot of U1,a.
《Fig. 3》
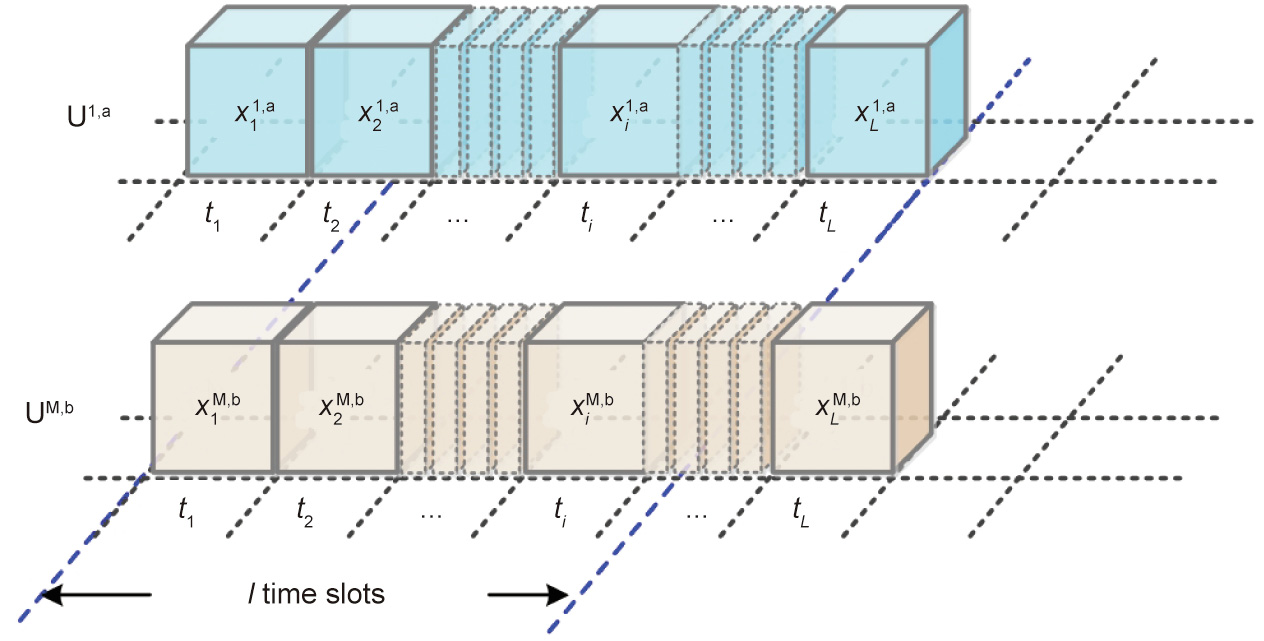
Fig. 3. Packet-transmission of U1,a and UM,b.  : the number of overlapping time slots between two packets in a transmission period;
: the number of overlapping time slots between two packets in a transmission period; 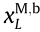 : the frequency slot that is occupied by UM,b at the Lth time slot;
: the frequency slot that is occupied by UM,b at the Lth time slot; 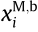 : the frequency slot that is occupied by UM,b at the ith time slot; tL and ti are the Lth and ith time slots, respectively.
: the frequency slot that is occupied by UM,b at the ith time slot; tL and ti are the Lth and ith time slots, respectively.
Theorem 1: Given the set of available frequency slots Fs with qs frequency slots, each available frequency slot  could be occupied by the authorized users with a probability of Pr
could be occupied by the authorized users with a probability of Pr  j = 1, 2, ..., q) If there are c time slots overlapping between two authorized users who access the HCNs asynchronously, when P1 = P2 = ···= Pq= 1/q, the maximum non-collision probability of these two users can be acquired, that is
j = 1, 2, ..., q) If there are c time slots overlapping between two authorized users who access the HCNs asynchronously, when P1 = P2 = ···= Pq= 1/q, the maximum non-collision probability of these two users can be acquired, that is

Proof: Without loss of generality, if two data packets occupy different frequency slots in each time slot, they can be regarded as not colliding. Considering that data transmission in different time slots is independent of each other, the non-collision probability of two data packets transmitted by U1,a and UM,b is
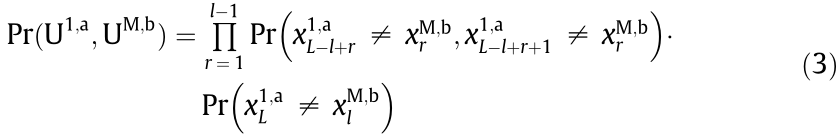
where 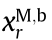 is the frequency slot occupied by the user Ub associated with BSM in the rth time slot, and r is a real number that goes through 1 to
is the frequency slot occupied by the user Ub associated with BSM in the rth time slot, and r is a real number that goes through 1 to  – 1. We assume that the probability of UM,b occupying the jth frequency slot in the rth time slot is
– 1. We assume that the probability of UM,b occupying the jth frequency slot in the rth time slot is 
Since the frequency slots occupied by U1,a in the tL-l+rth time slot and the tL-l+r+1th time slot are independent of each other, we can acquire that
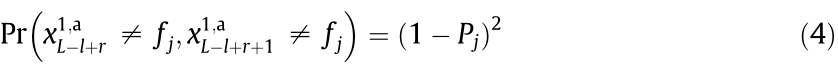
Similarly, when 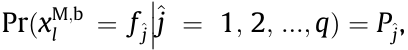 we can obtain that
we can obtain that

Considering that UM,b can randomly occupy one of the available frequency slots at the rth time slot and lth time slot, (i.e., 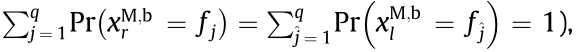 with the aid of the condition probability formula and the classical theory of probability, we can obtain
with the aid of the condition probability formula and the classical theory of probability, we can obtain
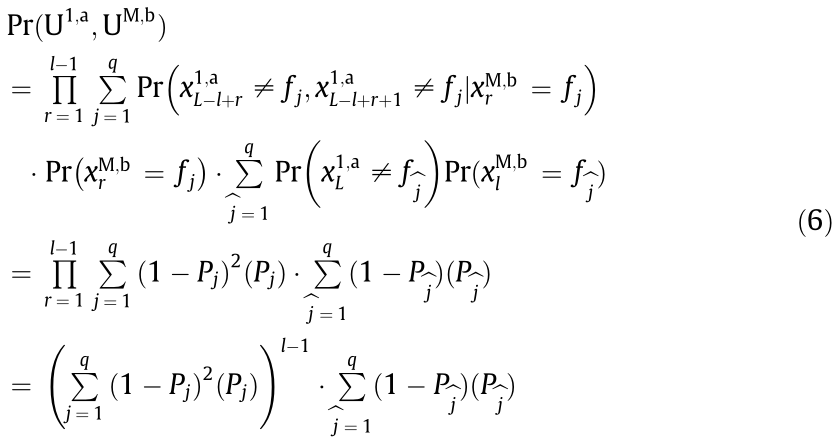
where 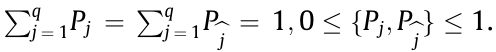
To obtain the maximum value of Pr(U1,a , UM,b), we formulate the Lagrangian multiplier expression 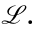
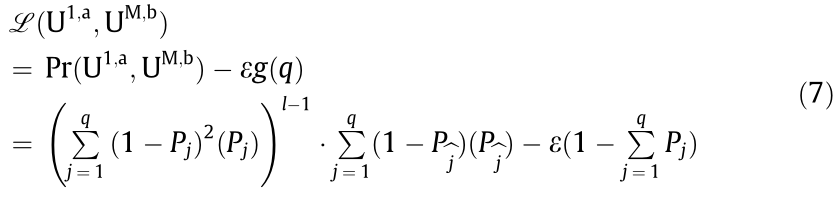
where ε is a real number representing the Lagrangian parameter; g(·) is a constraint function equal to zero.
Subsequently, we find the partial derivatives of 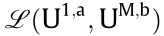 with respect to P1, P2, ..., Pq, ε, and set them equal to 0, then Eq. (8) can be acquired.
with respect to P1, P2, ..., Pq, ε, and set them equal to 0, then Eq. (8) can be acquired.
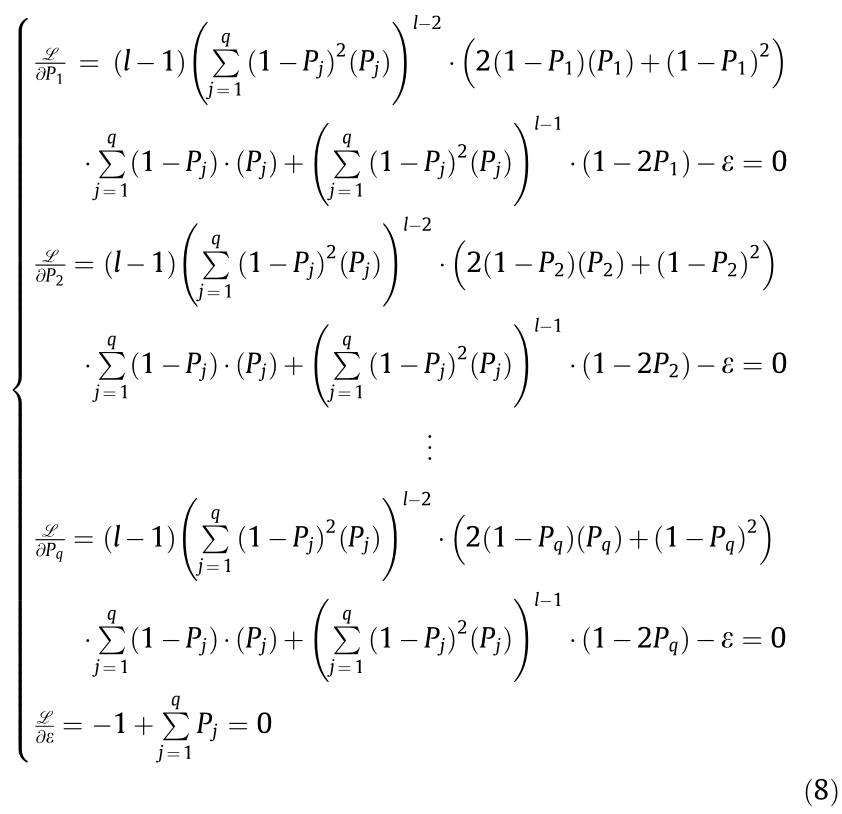
Since 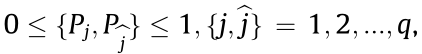 apparently only when P1 = P2 = ... = Pq = 1/q can Pr(U1,a, UM,b) obtain its maximum value. Therefore, the maximum value of the non-collision probability is Eq. (2).
apparently only when P1 = P2 = ... = Pq = 1/q can Pr(U1,a, UM,b) obtain its maximum value. Therefore, the maximum value of the non-collision probability is Eq. (2).
Therefore, only when all the available frequency slots can be occupied by authorized users with equal probability, the maximum value of non-collision probability can be obtained.
Based on the Theorem 1, we analyze the probability that n data packets can be transmitted without collision in HCNs.
Theorem 2: Suppose that the authorized users in our constructed HCNs can occupy the frequency slots in Fs with equal probability 1/q. When user Uφ,τ (τ {1, 2, ..., K}) is transmitting a data packet, there are k (k ≤ K) users that might collide with Uφ,τ (when φ = M, these k authorized users served by all the mBSs, when φ = 1, 2, ..., m, these k authorized users served by the MBS). Hence, the probability that Uφ,τ transmits a data packet without collision during the L data transmission time slots is
{1, 2, ..., K}) is transmitting a data packet, there are k (k ≤ K) users that might collide with Uφ,τ (when φ = M, these k authorized users served by all the mBSs, when φ = 1, 2, ..., m, these k authorized users served by the MBS). Hence, the probability that Uφ,τ transmits a data packet without collision during the L data transmission time slots is

Proof: Assume that the data transmission of authorized users U1,a and UM,b overlaps by  time slots. Since the process of the data packet arriving at the transmission channel follows the Poisson distribution, the probability for the authorized users transmitting the information at any time slot is equal. Accordingly, we can obtain that the probability of two data packets overlapping
time slots. Since the process of the data packet arriving at the transmission channel follows the Poisson distribution, the probability for the authorized users transmitting the information at any time slot is equal. Accordingly, we can obtain that the probability of two data packets overlapping  time slots is
time slots is
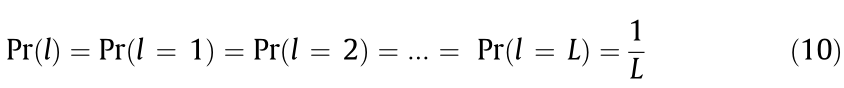
In our proposed DSC-assisted transmission scheme, the number of divided frequency slots should be controlled to be much larger than the number of time slots occupied for a data transmission, (i.e., q ≥ L). By leveraging a Taylor series and ignoring the highorder term, the above Eq. (11) can be further expressed as
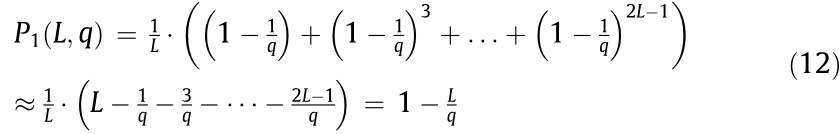
Hence, the non-collision probability between this data packet and all other k data packets is given by Eq. (9).
Two remarks can be derived from Theorem 2.
Remark 1: For a fixed k, Pr(L,k,q) is a power function of the ratio L/q, and this function monotonically decreases with increasing value of L/q.
Remark 2: For a fixed L/q, Pr(L,k,q) is an exponential function of k. In addition, since 0 < 1 –(L/q) < 1, Pr(L,k,q) decreases as k increases.
Corollary 1: Based on Theorem 2, the collision probability between Uφ,τ and k users in other base stations can be given by

where L  q. With the aid of the Taylor series, Eq. (13) can be further expressed as
q. With the aid of the Taylor series, Eq. (13) can be further expressed as

《4.2. Reliable transmission probability》
4.2. Reliable transmission probability
In HCNs, the interference to the transmitted information mainly comes from three aspects: background noise (N0), unauthorized malicious interference devices (Iun), and collisions between authorized users during data transmission (Ic). Therefore, the SINR of the authorized user (SINRu) can be expressed as

where Pu represents the power received by the authorized user from the associated BS, and Ic,u is the interference from other authorized users due to transmission collision. Note that the influence of unauthorized malicious interference devices on data packets transmitted by authorized users Iun,u can be avoided by Algorithm 1 (i.e., Iun,u = 0). Moreover, N0 is characterized by a zero-mean, complex Gaussian random variable. Similarly, the SINR of the eavesdropper (SINRe) can be presented by

where Pe is the power of the data packet received by the eavesdropper, and Ic,e denotes the collisions between data packets transmitted within the observed frequency slots of the eavesdropper and other authorized transmitted data packets. The interference of unauthorized signals to the frequency slots observed by eavesdropper Iun,e = 0.
As Wyner demonstrated in pioneering work [27], to decode the received data packet, the SINR of the authorized user should be greater than the decoding threshold (δu). We define the probability that all transmitted information can be received by authorized users as the reliable transmission probability, which can be expressed as

where SINRu,BS is the SINR of the authorized user associated with the BSM.
In the DSC-assisted scheme, the probability of the MBS occupying an available frequency slot  is Pr(fj). Then, the power of desired data transmission received by the authorized user (Pu,BS) can be expressed as
is Pr(fj). Then, the power of desired data transmission received by the authorized user (Pu,BS) can be expressed as
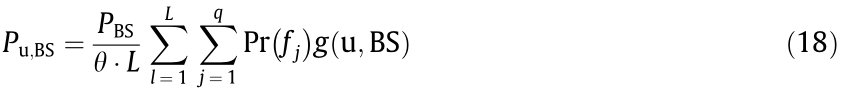
where PBS is the power of the BSM, θ is the number of authorized users associated with the BSM;  denotes the channel gain between the BSM and the authorized user at the lth time slot, which follows an exponential distribution with parameter α2 ; u indicates the authorized users. In addition, the interference power caused by other authorized users occupying the same frequency slot is
denotes the channel gain between the BSM and the authorized user at the lth time slot, which follows an exponential distribution with parameter α2 ; u indicates the authorized users. In addition, the interference power caused by other authorized users occupying the same frequency slot is
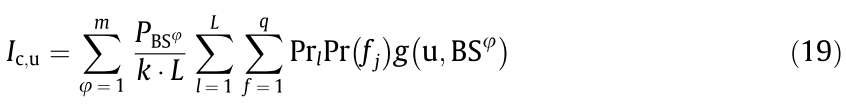
where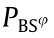 (φ = 1, 2, ..., m) refers to the power of the mBSs. In addition, we assume g(u,bs)=
(φ = 1, 2, ..., m) refers to the power of the mBSs. In addition, we assume g(u,bs)=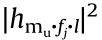 is the channel gain between the BSu and authorized user, which follows exponential distribution with parameter
is the channel gain between the BSu and authorized user, which follows exponential distribution with parameter 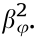
Upon substituting Eqs. (14), (18), and (19) into Eq. (15), the SINR of the authorized user can be rewritten as

Based on Eq. (20), we can now derive the following proposition.
Proposition 1: The reliable transmission probability for an authorized user receiving the data packet from the MBS given by

where Pbs indicates the power of the mBSs.
Proof: Please refer to the Appendix A.
Similarly, for an authorized user associated with mBS (BSφ, φ = 1, 2, ..., m), the reliable transmission probability can be expressed as
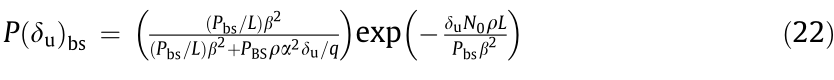
where ρ refers to the number of users served by the mBSs.
《4.3. Secrecy probability》
4.3. Secrecy probability
To prevent passive eavesdroppers from decoding the information transmitted between authorized devices, the SINR of any eavesdroppers should be lower than the decoding threshold δe.
Accordingly, we define the probability that valid information cannot be obtained by any eavesdropper as the secrecy probability, for example,

where SINRe,BS is the SINR of the eavesdropper observing the signal transmitted by the BSM.
Assume that eavesdroppers do not know the sequence family 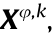 which is also the common case for most practical systems. Therefore, each eavesdropper associates a random frequency slot to intercept the transmitted data packet. Hence, when eavesdropping on the BSM transmission, the total power of intercepted data packets by the eavesdropper Ue (Pe) and the inter-cell interference to Ue (Ic,e) can be expressed as
which is also the common case for most practical systems. Therefore, each eavesdropper associates a random frequency slot to intercept the transmitted data packet. Hence, when eavesdropping on the BSM transmission, the total power of intercepted data packets by the eavesdropper Ue (Pe) and the inter-cell interference to Ue (Ic,e) can be expressed as

where e refers to the eavesdropper, the channel gain g(e,BS) =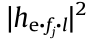 between the eavesdropper and the MBS follows an exponential distribution with parameter
between the eavesdropper and the MBS follows an exponential distribution with parameter  Similarly, the channel gain g(e,bs) =
Similarly, the channel gain g(e,bs) =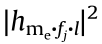 between the eavesdropper and an mBS obeys an exponential distribution with parameter ω2 .
between the eavesdropper and an mBS obeys an exponential distribution with parameter ω2 .
Substituting Eqs. (14) and (24) into Eq. (16), the SINR of eavesdropper can be rewritten as
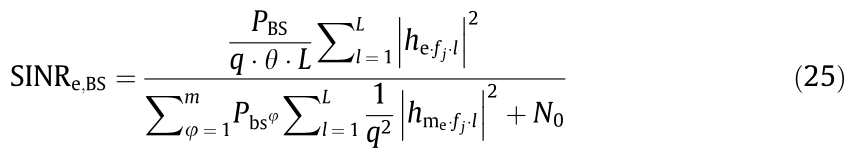
With Eq. (25), we can derive the following proposition.
Proposition 2: The secrecy probability can be expressed as
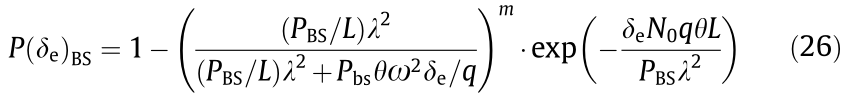
Proof: Proposition 2 can be verified in a similar manner as Proposition 1, so that the detailed proof is omitted here.
For an authorized user associated with the MBS, the secrecy probability can be expressed as

《5. Network capacity analysis》
5. Network capacity analysis
According to the analysis in Section 4, we can find that the reliable transmission probability and secrecy probability are both dependent on the number of users in the HCNs. Therefore, the upper and lower bounds on network capacity (i.e., the number of users that can be supported in the network) are derived in this section to guarantee reliable and secure data transmission probabilities.
《5.1. Network capacity of the MBS》
5.1. Network capacity of the MBS
Assuming that Pr,min is the minimum required reliable transmission probability in HCNs, the following relationship can be obtained according to Proposition 1.
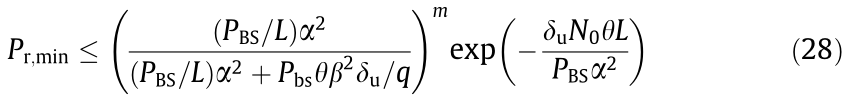
that is
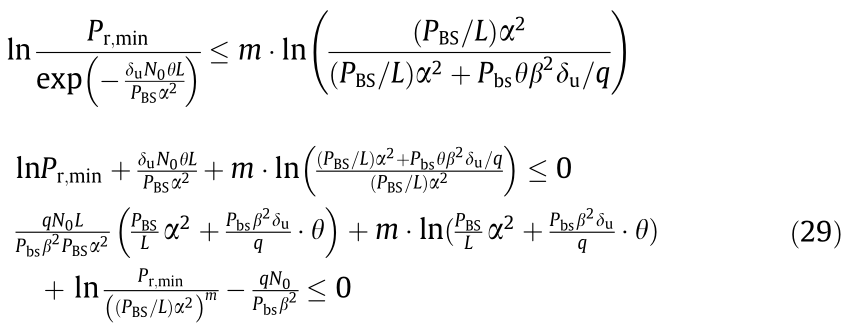
By leveraging the Lambert-W function, which is the inverse of xex , we can obtain that the upper bound of the network capacity of the BSM in HCNs is

where W is the Lambert-W function.
As long as the number of authorized users associated with the BSM does not exceed the maximum capacity of this network, the data transmission can be successfully completed.
Similarly, when the HCNs are constrained by the minimum secrecy probability (Ps,min), we can acquire the following relationship
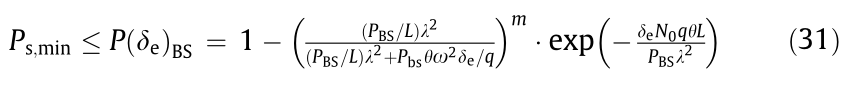
that is

With the aid of the Lambert-W function, we can derive the lower bound of this macrocell network capacity in HCNs under the constraints of Ps,min.
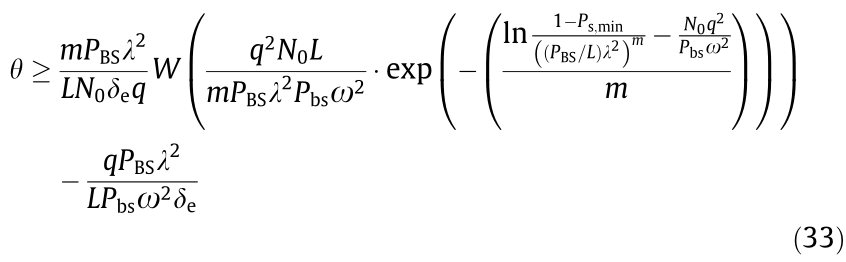
Therefore, the number of authorized users associated with the BSM should exceed the lower bound of the capacity to ensure that the data packets transmitted in the BSM cannot be decrypted by the eavesdropper.
《5.2. Network capacity of the mBSs》
5.2. Network capacity of the mBSs
Similar to the analysis in Section 5.1, the network capacity of the mBSs can be obtained. The upper bound of the mBS network capacity is
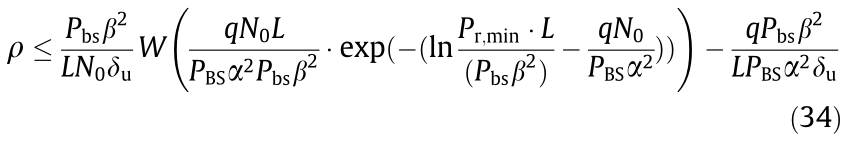
and the lower bound of the micro cell network capacity is
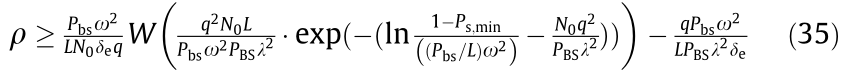
To this end, the upper and lower bounds of the number of authorized users allowed to access the network can be obtained according to the requirements of the actual application scenarios for the reliable transmission probability Pr,min and secrecy probability Ps,min of the HCNs. Therefore, by reasonably limiting the number of users accessing the network, the goal of effectively increasing the possibility of multiple users successfully transmitting data packets in the same transmission period while reducing the possibility of eavesdropping can be achieved.
《6. Numerical results》
6. Numerical results
In this section, we present simulation results to validate our theoretical analysis of the security and network capacity of HCNs. Moreover, we compare the proposed DSC-assisted transmission scheme with a benchmark scheme to demonstrate the effectiveness of the proposed scheme.
《6.1. Simulation configurations》
6.1. Simulation configurations
We consider a two-tier HCNs scenario, which consists of one MBS, and ten mBSs. Additionally, there are ten passive eavesdroppers were randomly distributed in our constructed HCNs. The powers of the MBS and the mBS are PBS = 43 decibel relative to one milliwatt (dBm)) and Pbs = 30 dBm, respectively. The parameter of average channel gain between the MBS and the authorized user is α2 = 5, for the channel between the MBS and the eavesdropper, it is 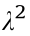 = 3. Similarly, for the mBSs, the parameter of average channel gain for the authorized user is β2 = 2, and for the eavesdropper is ω2 = 1. In addition, the bandwidth of the shared transmission channel is set to 300 MHz. Unless otherwise specified, all of the results in this section are obtained with the above parameter settings.
= 3. Similarly, for the mBSs, the parameter of average channel gain for the authorized user is β2 = 2, and for the eavesdropper is ω2 = 1. In addition, the bandwidth of the shared transmission channel is set to 300 MHz. Unless otherwise specified, all of the results in this section are obtained with the above parameter settings.
《6.2. Security performance evaluation》
6.2. Security performance evaluation
(1) Different SINR thresholds δu and δe: Fig. 4 shows the average reliable transmission probability and the secrecy probability with different signal-to-noise ratios (SNRs) when q and L are equal to 128 and 8, respectively. From the figure, we can find that
• The probability of reliable transmission increases with increasing SNR, while the secrecy probability decreases approximately linearly. This phenomenon is especially obvious when the SNR is in the range from –5 to 10 decibel (dB). This demonstrates that with the assistance of our proposed DSC-assisted transmission scheme, when the communication environment improves, the possibility of reliable transmission can increase rapidly, while the possibility of eavesdroppers intercepting the information also slightly increases.
• When the decoding thresholds δu and δe increase from 2 to 3, the probability of reliable transmission decreases, while the secrecy probability increases. This shows that with stricter requirements on the channel conditions for successful data transmission, HCNs become more vulnerable to security threats.
• We compare our proposed scheme with a conventional OFDM transmission method and an artificial noise-aided OFDM method [22]. The conventional OFDM transmission scheme aims to improve the resource utilization efficiency and achieve better network performance. Based on the conventional OFDM transmission scheme, the artificial noiseaided OFDM scheme introduces artificial noise to combat eavesdropping and enhance network security. We can find from the simulation results that the proposed DSC-assisted scheme can obtain the highest reliable transmission probability and secrecy probability. Furthermore, the proposed scheme does not introduce additional signal sources or require knowledge of the location of authorized users in advance. Therefore, it consumes less transmission power than the artificial noise-aided OFDM method and has a lower implementation complexity than the other two schemes.
• The theoretical results match well with the simulation results as shown in Fig. 4, which confirms the correctness of our theoretical analysis. In the following, we use theoretical results to evaluate the impact of different parameters on the performance of the proposed scheme.
《Fig. 4》
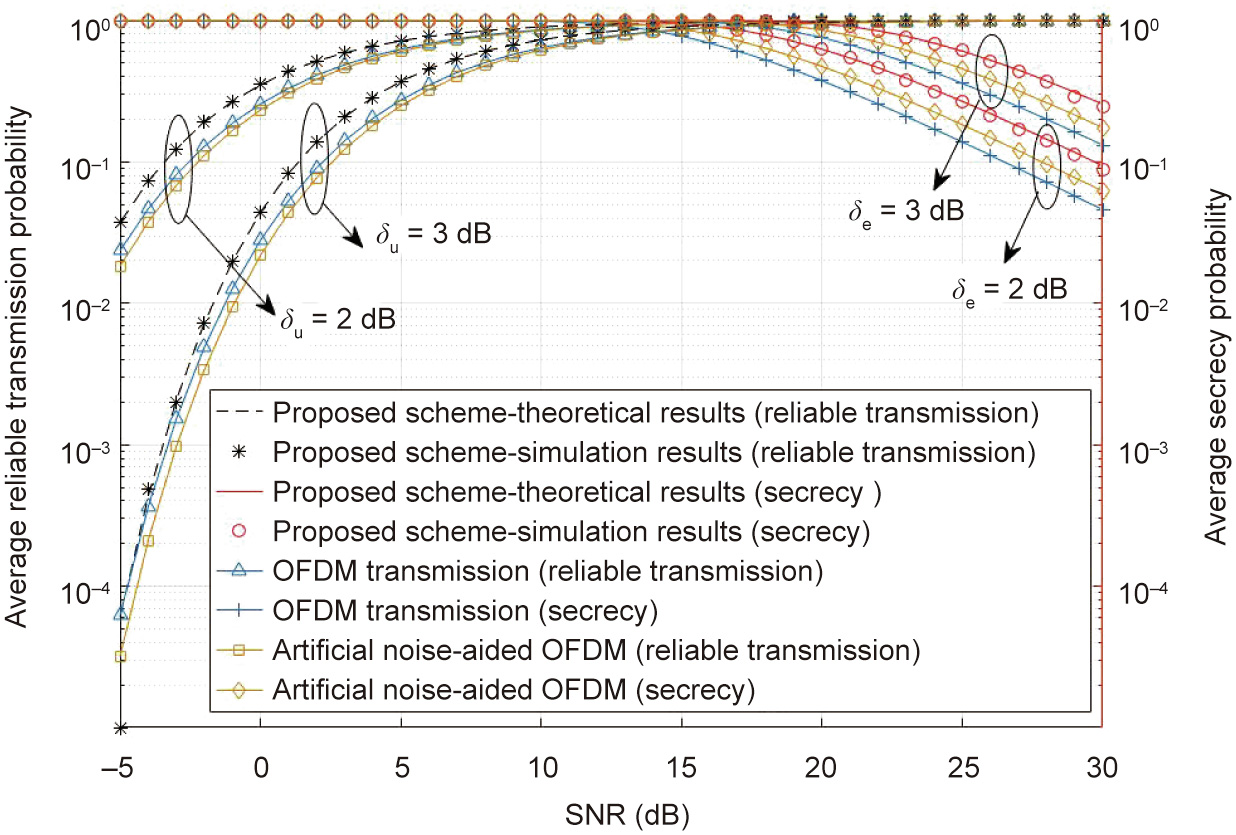
Fig. 4. Average reliable transmission and average secrecy probabilities vary with the SNR when q = 128 and L = 8. dB: decibel.
(2) Impacts of L and q on the reliable transmission probability: Fig. 5 demonstrates the influence of the time slot number L and the frequency slot number q on the average reliable transmission probability of the HCNs. The decoding threshold of the transmission link between the BSs and authorized users δu is 3. When each data transmission occupies L = 8 time slots, the reliable transmission probability increases as q increases. This is because dividing more frequency slots can effectively reduce the collision possibility among the data transmissions, leading to less co-channel interference among authorized users. In other words, it enhances the probability that the data packets can be successfully transmitted. However, when the available frequency slots number q is 128, as L increases, the reliable transmission probability decreases. The reason is that, with more time slots required for one data transmission, the collision probability increases with more co-channel interference.
(3) Impacts of L and q on the secrecy probability: We obtain the average secrecy probability curves in Fig. 6 with δe = 3. Different from the results in Fig. 5, the secrecy probability decreases with increasing SNR. Moreover, from Fig. 6, it is clear that the secrecy probability increases with a large L, when q is fixed. Once L is determined, the secrecy probability also increases as q increases. By utilizing the DSC-assisted transmission scheme, the eavesdropper has no idea which frequency slot is occupied for target data transmission in each time slot. If the eavesdropper always monitors one or several available frequency slots, it can only receive data fragments from different data packet transmissions. Since each data packet transmission occupies different frequency slots at different time slots, the eavesdropper has to successfully intercept all the data fragments to decode and obtain the entire data packet. With larger L and q, the eavesdropper needs to monitor more frequency slots for a longer time to obtain the complete data packet transmitted by the target authorized user. Therefore, with large L and q in the proposed DSC-assisted transmission scheme, it is difficult for the eavesdropper to decipher the transmitted data packets, leading to a high network security performance.
《Fig. 5》
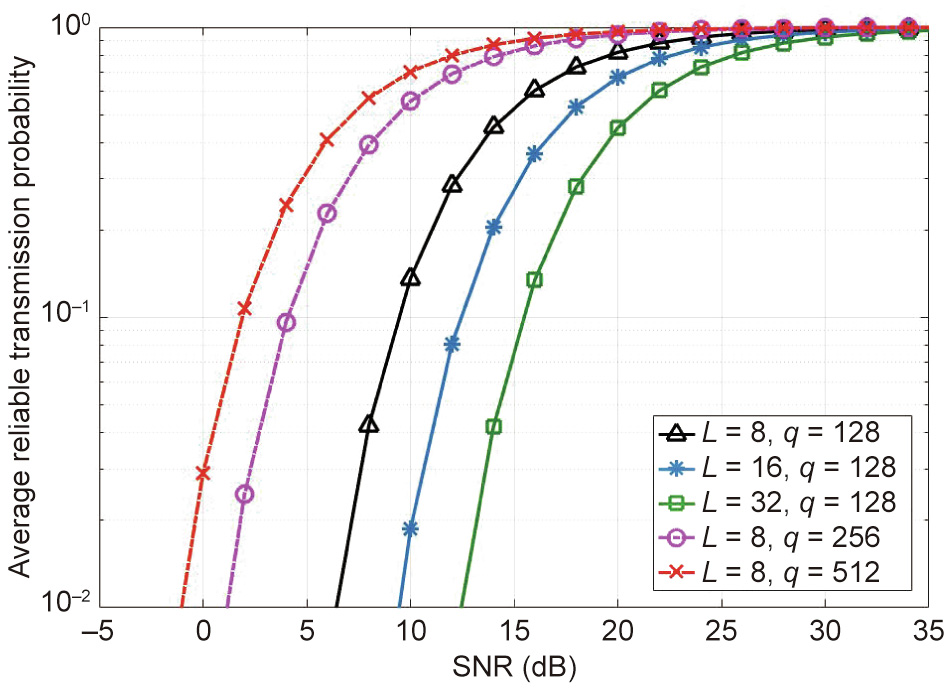
Fig. 5. Average reliable transmission probability variation with SNR under different L and q when δu = 3.
《Fig. 6》

Fig. 6. Average secrecy transmission probability variation with SNR under different L and q when δe = 3.
《6.3. Network capacity evaluation》
6.3. Network capacity evaluation
We examine the impacts of different parameter settings on the network capacity of the proposed scheme. Fig. 7 shows the network capacity of the HCNs when L = 8, and δu = δe = 2. Fig. 7(a) shows that as the minimum required value of the reliable transmission probability increases, the upper bound of the network capacity slightly decreases. This is because when the requirement for the successful transmission of data packets becomes stricter, fewer users are allowed to access the network to reduce the collision probability between data packets transmitted over the limited spectrum resources. Fig. 7(b) reflects that as the minimum required value of secrecy probability increases, the lower bound of network capacity increases. To make it more difficult for eavesdroppers to obtain data packets in HCNs, the number of users accessing the network should increase to introduce more possibilities of frequency slot occupation at different time slots.
《Fig. 7》
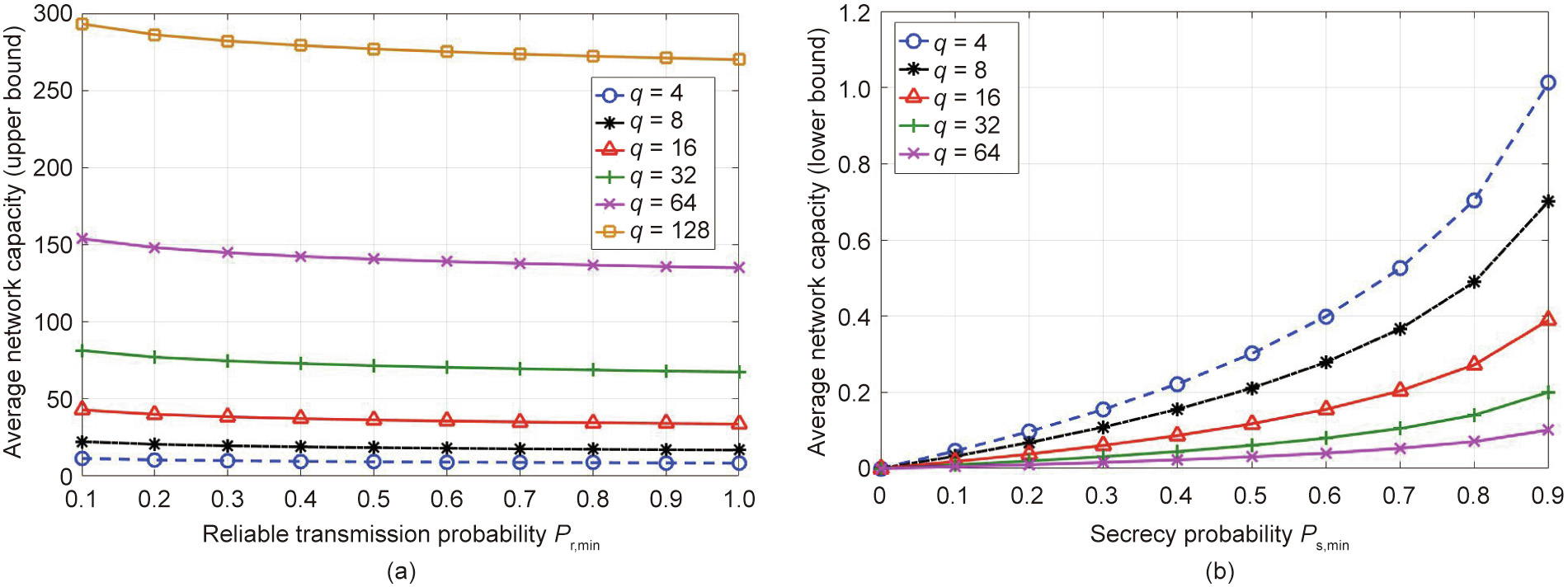
Fig. 7. Average network capacity variation with different requirements on reliable transmission probability and secrecy probability for PBS = 43 dBm, Pbs = 30 dBm, L = 8, and δu = δe = 2. (a) The impact of the reliable transmission probability requirement on the upper bound of average network capacity with different values of q; (b) the impact of the secrecy probability requirement on the lower bound of average network capacity with different values of q.
We can also find from Figs. 7(a) and (b) that, with a fixed Pr, min or Ps,min, a larger q indicates that more authorized users can be allowed to access the network. Furthermore, according to our simulation, for the cases with q greater than 128, the lower bound of the network capacity falls below 0, which means that the secrecy requirements of the HCNs can always be guaranteed regardless of the number of users in the networks. The above observations allow us to conclude that with fixed requirements on reliable transmission probability and secrecy probability, the parameters of the DSC-assisted transmission scheme can be adjusted to accommodate more users for reliable and secure transmission.
《7. Conclusions and future work》
7. Conclusions and future work
In this article, we have investigated the reliable and secure transmission problem in HCNs. Specifically, we have proposed a DSC-assisted transmission scheme to flexibly schedule the spectrum occupation for authorized data transmissions at different time slots. Moreover, we have also analyzed and derived closedform expressions of the collision probability, reliable transmission probability, secrecy probability, and network capacity. By adopting the proposed scheme, limited spectrum resources can be efficiently utilized, and the parameters of the DSC-assisted scheme (e.g., L and q) can be flexibly adjusted to enhance network capacity while guaranteeing secure transmission. The scheme design and theoretical analysis in this work can provide useful guidance for future research on security enhancement of wireless networks. For our future work, we will introduce friendly interference sources and investigate source selection and power allocation to further improve the reliable and secure transmission probabilities.
《Acknowledgments》
Acknowledgments
This work was supported by the National Natural Science Foundation of China (61825104 and 91638204), the China Scholarship Council (CSC), the Natural Sciences and Engineering Research Council (NSERC) of Canada, and University Innovation Platform Project (2019921815KYPT009JC011).
《Compliance with ethics guidelines》
Compliance with ethics guidelines
Chenxi Li, Lei Guan, Huaqing Wu, Nan Cheng, Zan Li, and Xuemin (Sherman) Shen declare that they have no conflicts of interest or financial conflicts to disclose.
《Appendix A. Supplementary data》
Appendix A. Supplementary data
Supplementary data to this article can be found online at https://doi.org/10.1016/j.eng.2021.04.019.













 京公网安备 11010502051620号
京公网安备 11010502051620号




